Azure AD
Support of Groups in Active Directory
The automatic group mapping is currently not supported for Microsoft Active Directory. [Due to this]
It is possible to setup Azure Active Directory together with the piplanning app as an OpenID provider. With this setup in place, your existing Azure AD users will be able to login to the piplanning app without the need for a different account.
The generic instructions are also available on the Microsoft Docs website
Setting up Azure AD
- Go to the Azure portal: https://portal.azure.com/#home
- Select Azure Active Directory in the menu
- Go to App registrations and click on New registration
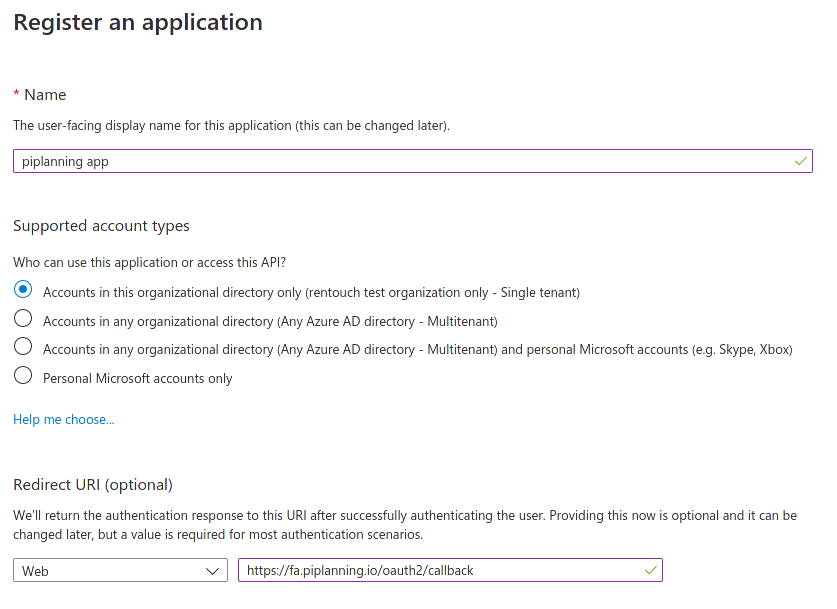
- Insert the name of the application (e.g. piplanning app) and the callback URL.
Please note: Depending on how your AD is configured and which users you want to give access to the piplanning app, you might have to select a different option in the Supported account types section. If login for some users doesn't work, try changing this configuration option.
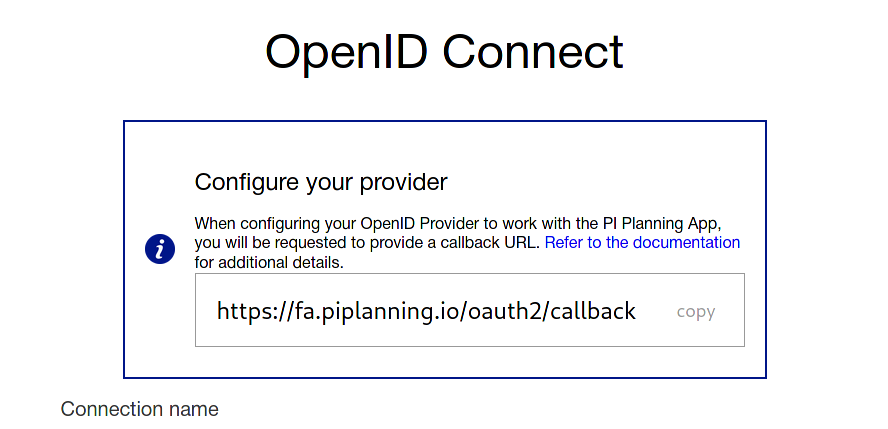
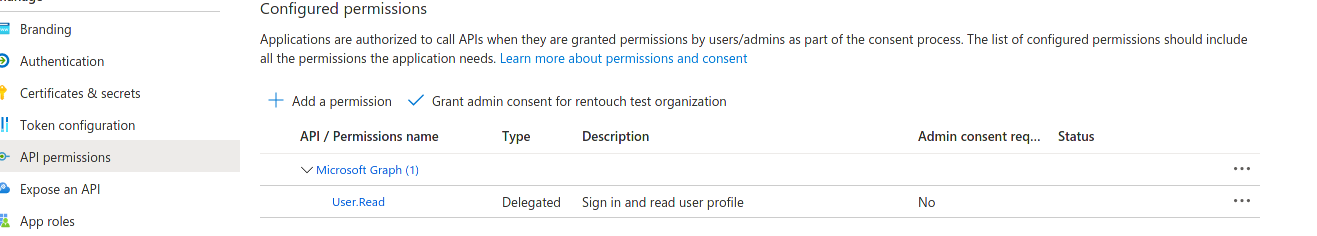
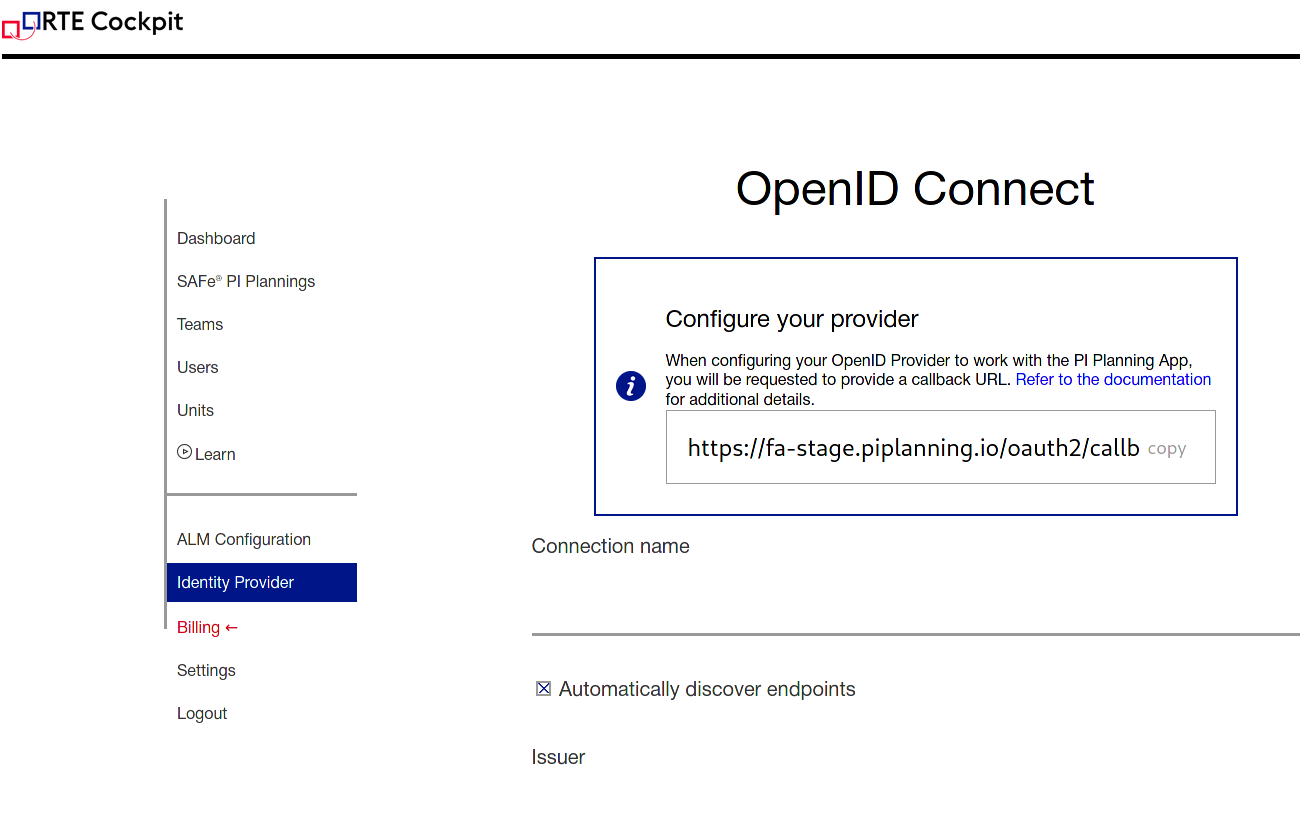
The callback URL can be found on the "Identity Provider" page in the Cockpit. - Double check that the permissions are correct. You need the Microsoft Graph User.Read permissions to be able to login successfully.
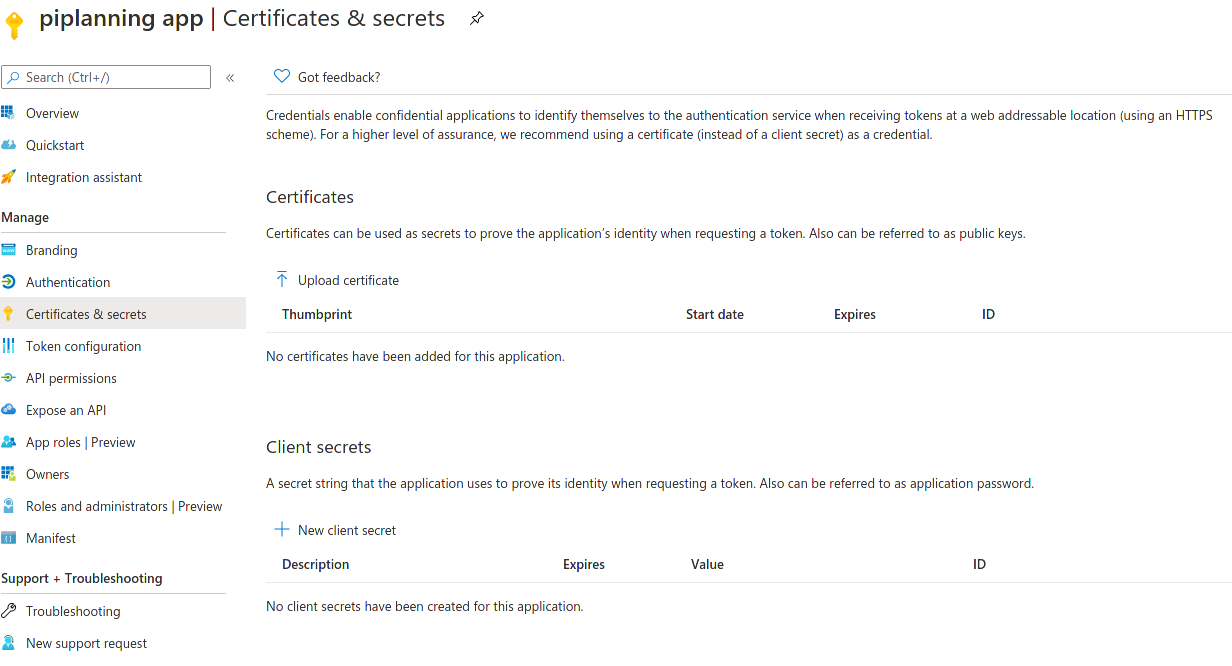
- Next is the creation of a client secret. This can be done by going in the "Certificates & Secrets" menu item and clicking on "New client secret"
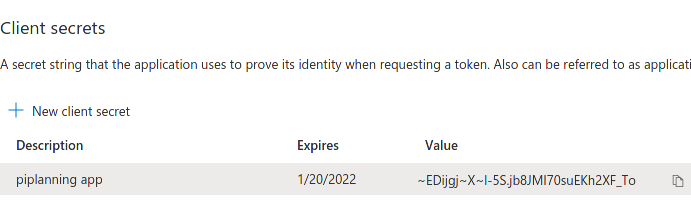
- The secret can now be copied and saved. This information is needed in the piplanning app to setup the Identity Provider
Setting up the piplanning app
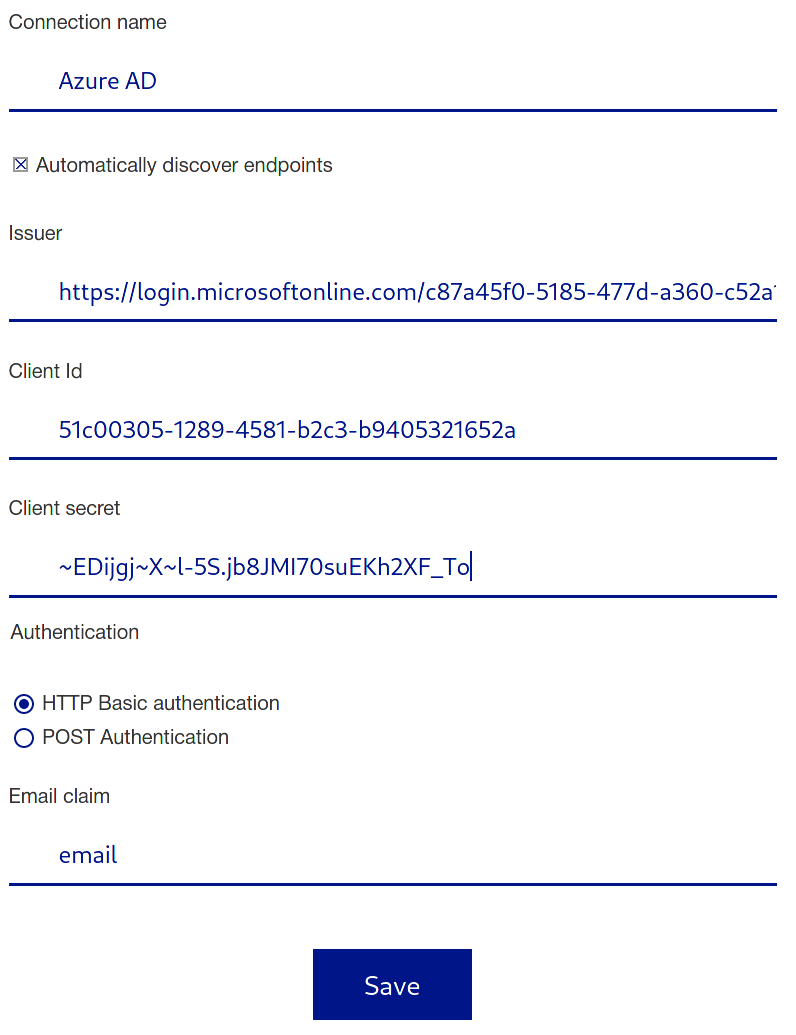
- Login to the Cockpit and click on the "Idenity Provider" menu item. The OpenID Connect configuration page will open.
- Fill in a connection name of your choice. This name will appear on the login button for your users. (e.g. "Azure AD")
- Leave the "Automatically discover endpoints" option enable and enter as Issuer the following URL: https://login.microsoftonline.com/{tenantId}/v2.0
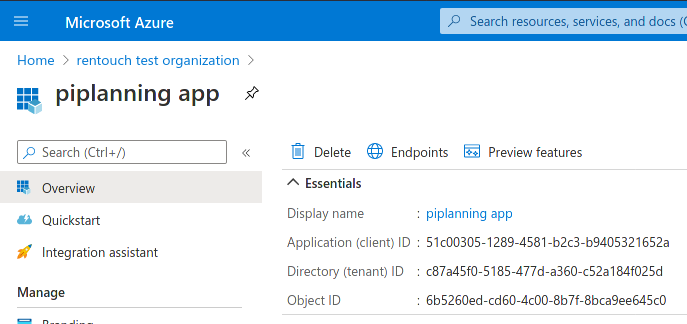
The tenant ID must be substituted with the value found on the Azure AD application registration overview as Directory (tenant) ID:
Please note: Depending on your configuration, you might have to use the older version of the API. If login doesn't work with your setup, try to remove /v2.0 from the issuer URL:
https://login.microsoftonline.com/{tenantId} - Fill in the client ID that you can also find in the application registration overview as Application (client) ID
- Fill in the client secret from the value you previously generated under "Certificates & Secrets"
- At this point the form should be complete and by clicking "Save" the connection should now be saved.
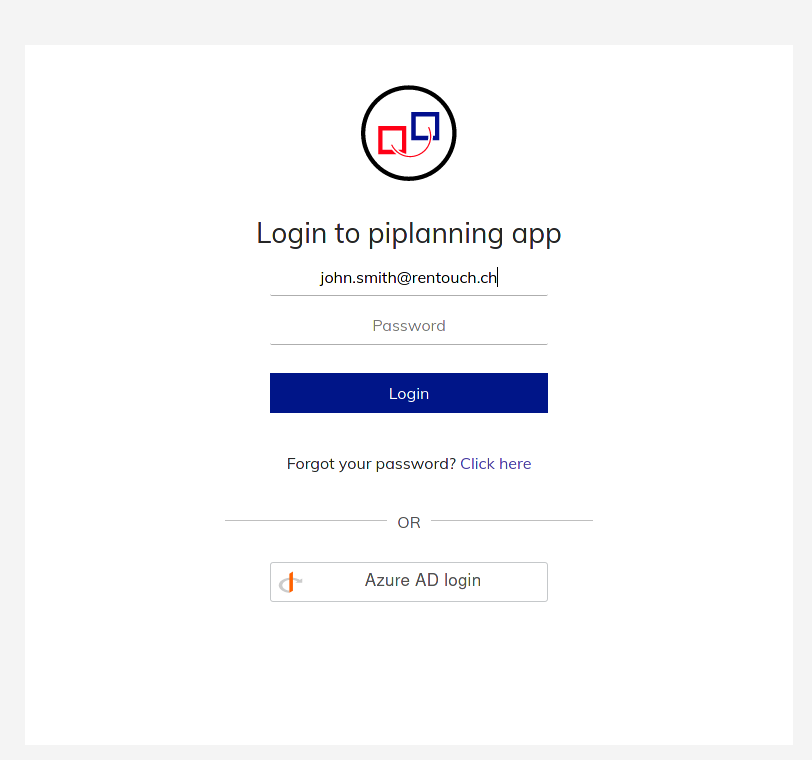
The login screen will now add the option of logging in with Azure AD
FAQ
Q: During login, I get the error: "A request to the OpenID Connect Token API has failed. Unable to complete this login request" [Backend error: AADSTS700025 - invalid_client]
A: Make sure you have selected "Web" (instead of single page application) for the redirect URI in Azure.